Clinton-Connected Operatives Attributed DNC Hack To Russia
Attribution report released: New questions
The DNC hack is nothing but fraud, the attribution is wrong, and our government has engaged in a criminal cover up at the highest levels. No doubt the hackers indicted by Special Counsel Mueller are guilty of a great many crimes, but in our justice system we don’t indict bad people for crimes they didn’t commit.
A freight train has been rolling down the tracks since the last word on the hack by the “experts” in Mueller’s final report. At the helm of the locomotive are a small number of sources who have been telling the same story; the Department of Justice, the FBI, and Special Counsel Mueller relied, at least in part, on a small band of cyber researchers tied to Hillary Clinton. Documents obtained through a painstaking process of Freedom of Information Act requests, state-FOIA equivalents and resulting litigation have drawn out the contours of this relationship, but over 6 years since the Russians were indicted for the hack, nobody has double checked Mueller's work.
In the summer of 2016, Georgia Tech cyber researchers who worked as part of a “joint-venture conspiracy” with Clinton campaign officials and Fusion GPS submitted an attribution report on the DNC hack at the same time as they were spawning allegations of a secret communications channel between Trump and Putin. Manos Antonakakis and David Dagon, referenced as Researchers 1 and 2 respectively in the indictment of DNC attorney Michael Sussmann, were previously known as key players in the Alfa Bank allegations.
In October 2016, sources approached the FBI and identified David Dagon as the author of the technical white paper purporting to support the existence of a secret communications channel. A pressure campaign saw Christopher Steele include Alfa Bank in his dossier after a series of meetings with Clinton campaign operatives, and Steele produced his Alfa Bank memo to the FBI in the first week of October 2016. L. Jean Camp of Indiana University would publish the data around that same time, and April Lorenzen created a blog behind the pseudonym “Tea Leaves” on October 5, 2016 with the allegations. A second dossier written by Clinton operative Cody Shearer appears to allude to the Alfa Bank allegations despite being authored before the purported DNS lookups ever began, and that dossier was given to the State Department (and later the FBI) in September 2016.
Circular reporting is a signature of the Russiagate smear campaign that was perpetrated, and it was seen again and again. Fusion GPS would arrange meetings with journalists and give them dossier materials, and then the FBI would take the dossier reports from Steele and the public reporting that purported to be independent corroboration and they used it all as support for FISA warrant applications.
At every turn there was a pressure campaign using the media as a weapon.
The DNC hack is no different.
At some point, guarded reporting must give way to accepting the truth presented in numerous documents. In emails and letters the cyber researchers indicated they submitted an APT-28 attribution report on the DNC hack, and later were tasked “via DARPA” to work for Special Counsel Mueller. That’s right. The Special Counsel that was the subject of daily news coverage for years and defended as running an independent and non-partisan investigation was in fact, placing reliance upon operatives tied to Hillary Clinton who already had a suspicious connection to debunked Alfa Bank allegations.
FireEye once described APT-28 as a highly sophisticated cyber organization that likely employed hundreds of programmers owing to their incredible ability to commit zero-day exploits. So it was hard to believe that they would break their pattern by adopting an online pseudonym, Guccifer 2.0, to release documents after committing so many mistakes. They used Russian-language settings and immaterially modified the documents, leaving Cyrillic characters as well as metadata behind containing a profile in the name of a famous Soviet head of police who died in 1926. They reportedly forgot to turn on a VPN, and re-used an IP address that had been blown - publicly associated with APT-28 already.
They used an AOL email account that is known to provide IP address information, and then secured the account Guccifer20@aol.fr with a password of ‘Guccifer20’, and a cell phone that appears to be a mobile number in France. They chose a moniker of Guccifer 2.0 weeks after Guccifer A.K.A Marcel Lazar was announced to have hacked Clinton’s email server, likely helping to obscure continued stories about Clinton’s emails. When the DNC hack was announced in the Washington Post, they titled it “Russian government hackers penetrated DNC, stole opposition research on Trump”, but according to testimony from Shawn Henry of Crowdstrike, they had no indication from Crowdstrike’s sensors that anything had been exfiltrated. In other words, nobody knew for sure that any files had been stolen until Guccifer 2.0 emerged the day after the Washington Post article and published the opposition research. Someone interviewed by the Washington Post had information they weren’t supposed to have. We’ll revisit this later.
The House Intelligence Community noted that redacted Crowdstrike reports arrived in late August and Jim Trainor of the FBI suspected they had been “scrubbed” by Michael Sussmann. Yared Tamene, an IT contractor for the DNC, testified to his understanding that Crowdstrike transmitted the forensic images of the systems in May or June of 2016. In truth, the data and server images from the DNC were still being requested by the FBI in October 2016, after the government formally attributed the hack to Russia on October 7, 2016.
Things never made sense for the Steele dossier or the Alfa Bank allegations. When all was said and done, it was admitted that portions were complete fabrications. The DNC hack is one and the same, an integral part of a criminal conspiracy.
The Georgia Tech cyber researchers told the New York Times their research into DNS activity began in the wake of the DNC hack disclosure while at a M3AAWG conference. Emails obtained from Georgia Tech in 2022 indicated that these cyber researchers had some nexus to a report on the DNC hack attribution and the Mueller investigation, which DARPA immediately denied. Upon inquiries from Senator Grassley and Senator Johnson, DARPA walked that back and admitted that an August 7, 2016 attribution report on the DNC hack existed, offering that it was done “likely to highlight the capabilities of their technical approach.”
Emails indicate the August 7, 2016 report is one of a series of reports related to the DNC hack produced by the cyber researchers, including one document described as a list of domains and indicators of APT-28 produced for Special Counsel Robert Mueller. DARPA’s latest explanation was that this document related to the Mueller indictment of the Russians but it was retrospective. Once again, DARPA appears to be lying or uninformed. Emails and letters obtained through Open Records Requests do not support any assertion that this work was retrospective, rather, it appears that their work plays a critical role in the Mueller indictment of Netyksho et al.
A lengthy court battle has resulted in the August 2016 document being released.
Cyber experts who have reviewed the document suggest the cyber researchers suffered from confirmation bias, and appear to have started with the conclusion that Russia hacked the Democratic National Committee. The unredacted portions of the analysis appear to identify domain registrations purportedly tied to APT-28 and crypto currency transactions in support of those domain registrations. At least one portion of their analysis appears to relate to Domains4Bitcoins, which is a company headquartered in Wisconsin and flagged by ThreatConnect.
The report contains a curious similarity to explanations offered for their Alfa Bank allegations, offering suggestions “to those who have more resources for a deeper investigation”, before going on to suggest a series of subpoenas and investigative steps. This may demonstrate their understanding that their report would be transmitted to law enforcement agencies, an understanding outlined in a 2020 letter from David Dagon’s attorneys:
The report, described as amateurish by professionals in the industry, contains at least one oddity, a figure denoting the geographic distribution of a redacted observation that appears to suggest some activity occurred out over the open ocean:
The report also observes “attributes of an attack on an electoral system” weeks before news broke of Russian hackers targeting the State Election Boards in Arizona and Illinois.
Prophetically, the report suggests that Russians may try to influence the election using social media “web brigades”, a narrative that persisted for years with little evidence.
Additional emails obtained through litigation from the email account of DARPA’s former head of the Enhanced Attribution program, Angelos Keromytis, references a mysterious report circulating between August and October 2016, with the email chain ending with a “DARPA and White House only” meeting on October 7, 2016.
That afternoon at 3:29pm, DHS and ODNI would release their joint attribution statement formally accusing Russia of the hack for the first time.
New Questions For Neustar
In 2015 Neustar lost nearly half their revenue when a final decision was made to award the next Number Portability Administration Center contract to Telecordia. Neustar engaged in a significant lobbying campaign against Telecordia in an attempt to save the contract.
Billing records produced during the trial of Michael Sussmann frequently refer to work done on the Alfa Bank allegations as the “confidential project”, with the first reference dating to January 2016 on an invoice paid by Neustar, months before the DNS lookups at issue in the Alfa Bank allegations.
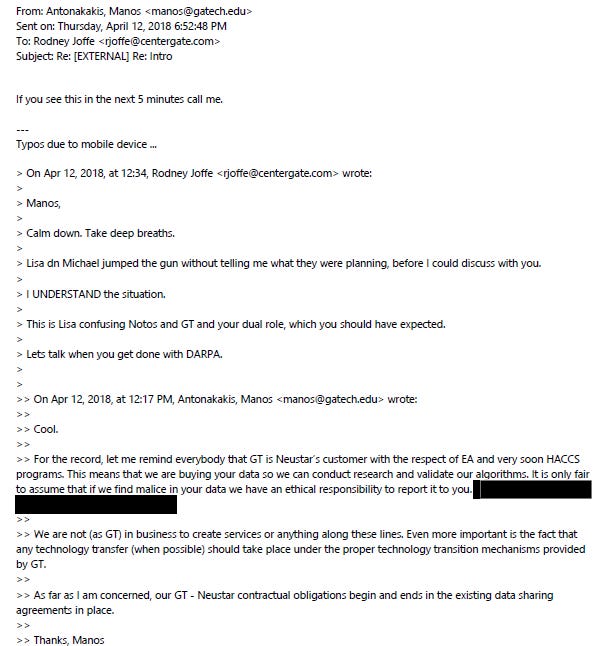
A 2022 lawsuit filed by “Tech-Executive-1” Rodney Joffe against Neustar sought $2.6 million in reimbursement of legal fees, suggesting more extensive legal work than previously known (at a billing rate of $1,000 an hour, that would indicate over 2600 hours of billable work). Within the complaint (#12), Joffe suggests that Neustar’s CEO, Lisa Hook, was aware of his work on the Alfa Bank allegations and “other matters” and approved of it.
Sources have consistently suggested that Rodney Joffe played a role in the DNC hack attribution, dating to before the existence of the Dagon-Antonakakis attribution report was known. The scuttlebutt at Neustar was that Rodney Joffe had traced the hack of the DNC back to Russia for the government. Through counsel, Joffe vehemently denies any knowledge of, or involvement in, Dagon and Antonakakis’ work regarding the DNC hack or in the DNC hack attribution more broadly. To believe that, you need to accept that while Antonakakis and Dagon worked closely with Joffe on the Alfa Bank allegations over the course of months, they never mentioned they were performing an attribution assessment on the DNC hack at the same time using data provided by Neustar, where Joffe was a senior executive. To be fair, there are no public documents or indications from numerous investigations that Joffe had any role in the DNC hack attribution. The closest data point came from the Sussmann trial, when it emerged that Joffe had assisted the FBI with Russian cyber matters.
At the same time, no investigation has disclosed the existence of the Dagon-Antonakakis attribution report or the scope of their work for Special Counsel Mueller. Whether the reports of Joffe’s involvement are based on a misunderstanding in Neustar providing data to the Georgia Tech cyber researchers and Joffe’s prior work in Russian cyber matters, or whether there is yet another attribution report out there, remains to be conclusively answered.
A peculiar email chain from 2018 between Antonakakis, Joffe, Sussmann and Neustar CEO Lisa Hook suggests the possibility of “malice” in Neustar’s data:
It remains unclear if there were any discussions between the Clinton campaign and Neustar about restoring the NPAC contract if Clinton were to win.
It also remains unclear if the Department of Justice and FBI were aware of these data concerns before entering into a series of memorandums of understanding with DARPA that enabled DARPA and its contractors to assist with criminal investigations that include the Tree of Life Synagogue shooting and Harold T. Martin, the former contractor who stole 50 terabytes of data from the NSA. In current FOIA litigation, the DOJ has suggested that a foreign actor could tamper with this attribution model if the inputs were disclosed. Could a domestic actor do the same?
Circular Reporting?
What prompted the Georgia Tech cyber researchers to do an analysis of the DNC hack? In letters and emails sent during negotiations with Georgia Tech to pay their legal expenses, the cyber researchers repeatedly represented that DARPA had asked them to look into Guccifer 2.0, apparently on behalf of the Department of Justice with whom DARPA also maintained a series of memorandums of understanding. DARPA for its part has repeatedly denied any tasking of the cyber researchers or knowledge of any assignments.
The proximity in timing to their Alfa Bank allegations suggests their work might have been done at the behest of the Clinton campaign with whom they were in contact with via Michael Sussmann.
The report could be seen as carrying the trademark signature of other narratives sprung by the Clinton campaign, the same information being funneled to the government through multiple vectors purporting to be independent of one another. Without the hack of the DNC, it’s challenging to see the utility of Fusion GPS who had been engaged by the Clinton campaign just weeks before the purported hack began to investigate Trump’s alleged ties to Russia. Was the hack a serendipitous gift to opposition researchers?
A small band of cyber researchers tied to the Clinton campaign are connected to every piece of the Russiagate narrative. The precise scope of their involvement will require piercing the Grand Jury secrecy in the Netyksho case and interviews with members of the Mueller team who wiped dozens of phones.
Attribution
What went wrong?
Cyber attribution is a hotly contested subject in the cybersecurity industry. We saw that in one email chain first obtained by Margot Cleveland of The Federalist between Wenke Lee of Georgia Tech and Manos Antonakakis. In the middle of a heated exchange, Dr. Lee asks an important question on Antonakakis’ method of cyber attribution, “You see attack traffic coming out of China, and China says it is routing traffic for other countries, e.g., North Korea. What do you do to know that it is China vs. North Korea, or you don't care (e.g., just blame on China).”
Antonakakis responds by saying “You do not attribution like this Wenke. You do attribution from studying the mistakes they do during an operation. China, Greece or Mars, is actually irrelevant.”
Dr. Lee’s question is the critical point. There is no dispute that the alleged DNC hack was launched from technical infrastructure known to be associated with Russia. The issue is that anyone familiar enough with DNS can do the same thing emulating the tactics, techniques and procedures of a known malign group.
In his next response, Dr. Lee gives us some additional important insights:
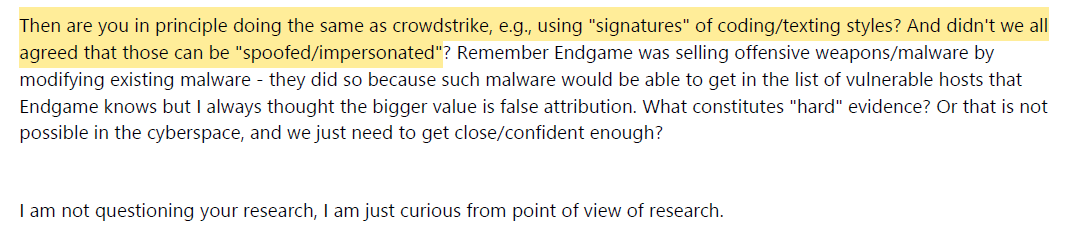
Dr. Lee notes that Crowdstrike’s attribution methods are considered spoofable, and then goes on to point out that modifying existing malware can be an excellent means to have false attribution. This is highly relevant to the DNC hack because some portion of the malware was purchased by the alleged hackers and then modified. Presumably, cyber researchers working on APT-28 hacks would also accumulate portions of malware.
Dr. Lee had one more relevant item in the exchange. “I was not talking about signatures of malware, I was saying that if you are using signatures/signals of traffic and if those can be (easily) spoofed/impersonated, then in principle your approach would suffer the same weakness (spoof-able) as CS.”
The Dagon-Antonakakis attribution methods are also considered spoofable.
The FBI never analyzed all the servers. The entity the government told us they relied on [Crowdstrike] uses methods considered spoofable and only had “medium” confidence in their attribution assessment when it was given to the FBI. The people the government appears to have actually relied on are tied to the Alfa Bank allegations and the Clinton campaign.
Cyber professionals familiar with attribution work make the crucial point that merely using technical analysis is not enough to attribute a hack like this. It requires a broader analysis of the adversary and the victim. The DNC hack must be placed in a broader context and we must ask why Christopher Steele included the hack in his dossier. We know now that Steele was a mouthpiece of narratives that Clinton wanted. Why would Steele fabricate motives and other claims for the DNC hack?
Netyksho Indictment
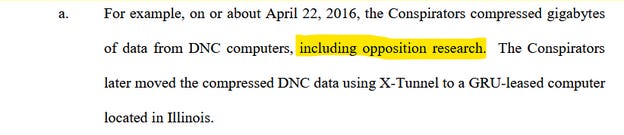
Mueller’s indictment is rife with inaccuracies, imprecision, and unsubstantiated assertions. As just one example (and there are many), Mueller offers this:
We know that the emails were primarily exfiltrated between May 23-25 because the vast majority of them are dated through that time. The DNC had a 30 day retention set up on their email accounts. What about this April 22 date? Shawn Henry of Crowdstrike described it as follows:
Here’s the rub. That Trump opposition research document does not show up in the DNC files uploaded to Wikileaks. In fact, of the initial batches of files released by Guccifer 2.0, none of them were published by Wikileaks as being from the DNC. A number of them, like the Trump opposition document, show up in the leaked emails from John Podesta, and a larger number are completely unaccounted for as to their origin.
Mueller suggests without evidence that the opposition research document was part of the documents stolen from the DNC on April 22, but the only conclusively stolen documents weren’t taken until late in May. Why would the hackers compress any data and then not exfil it immediately? Why would they register domains like DCLeaks.com before they had stolen any documents?
Intentional obfuscation? This paragraph of the indictment serves as the lone data point towards an unspoken explanation for the Washington Post article. We are led to presume that there must be some unseen technical support indicating the opposition research was stolen from the DNC and not just from John Podesta, despite Crowdstrike having no evidence of exfiltration and the document not showing up on Wikileaks as part of the DNC files. If there is an absence of technical support, the conspiracy takes form with yet another example of weaponizing the media to advance a narrative.
Ursine Undertaking
It’s time to call bullshit.
It’s the worst political scandal in history. The level of planning and coordination needed to pull this off and cover it up for 8 years is more than a handful of operators at a political campaign could muster. Maybe the Georgia Tech researchers were unaware of tampering with data they used but there is no question that there were elements of the Obama administration who were willful and knowing co-conspirators. That the Mueller team wiped dozens of phones is now looking like obstruction of justice in the concealment of material evidence favorable to the defendants of the Netyksho case.
If the Department of Justice wants its credibility back it needs to declassify and release everything. Prove me wrong. Prove my sources wrong.









Fantastic stuff. Thank you. I know how incredibly hard you have worked. Gotta feel great it is all paying off.
The last thread of the net of lies is unraveling.
I have a few questions, particularly about the timing of the attribution release okay by the Obama administration (i.e., Obama) and what they had and what the FBI had and that meeting the same day with the White House.
Let me soak on it a while, reread, and see if I can pose the questions cogently.
Also, could you say these sentences in another way? I want to make sure you are saying what I think you are saying. (Oops-- I will cut and paste them below.)
Lastly-- will you please do one of those things where we can ask you questions sometime after Christmas? Soon, but enough time to go back over stuff and gather thoughts.
Thanks for doing this. If state media ignores it, which they will, no one will ever know. Can you get on FOX? Do you have an agent?