A Cup of Joffe
This week, I connected with Rodney Joffe for the second time (through counsel) as I continue work on a substantive story. While I work on that, I thought I would offer a few pieces of our discussion.
Mr. Joffe (through counsel) stated he never worked on the DNC hack attribution, and had no awareness or insight into that investigation other than what has come out in public reporting.
I then asked a more pointed question making reference to testimony from FBI Agent Thomas Grasso (pg 111):
My question referenced the CHS label applied to Joffe during the Sussmann trial. They offered an explanation on that point first:
“As you know, it has been widely reported that Mr. Joffe has provided assistance to the FBI over the course of many years. I believe that even in your own posts you have carried the public information regarding the FBI Director’s Award that was presented to Mr. Joffe for his work related to a specific criminal cybersecurity gang that he helped identify and bring to justice. As a cybersecurity expert he has assisted Law Enforcement in scores of both criminal and national security investigations during his long career. But you may be confusing this with Mr. Joffe being a CHS (Confidential Human Source) in the way that moniker is commonly used. Mr. Joffe has never been an employee of, or a “paid informant” for the FBI, or indeed any other Law Enforcement or Government entity. Like many thousands of other concerned citizens, when Mr. Joffe has become aware of activities that are a threat to the public or to national security, he has notified the appropriate official organizations of his findings for them to evaluate and take action, if warranted.
Because of the concerns of some of those organizations for Mr. Joffe’s safety when his information has resulted in investigations of vindictive criminals or adversarial foreign actors, he has sometimes been identified within those organizations with a coded reference rather than by his name and address to protect his personal safety, as is common. It is under that circumstance that he was referred to as a “CHS” by the FBI. Nothing more. He was never an “informant”, paid or unpaid.”
They went on to address my question of whether he had provided assistance to the FBI relating to the DNC hack attribution:
As an expert, Mr. Joffe also has often been approached by Law Enforcement and other official investigatory entities who requested his help with issues that they believed Mr. Joffe’s expertise could assist in. The FBI is no different. Mr. Joffe has provided assistance to them over the years in matters that relate to criminal and national security threats involving a number of the United States’ adversaries, including Russia. However at NO time did the FBI or ANY other person or entity contact Mr. Joffe in any way and ask for assistance regarding the “DNC Hack”. Mr. Joffe did not personally contribute in any way to the investigation before it was made public (reiterating his earlier statement that the very first he was aware of the “DNC Hack” was when it was made public in the press), and he was not asked for and provided no assistance whatsoever to the FBI or anyone else in any investigation of the “DNC Hack” after it became public.
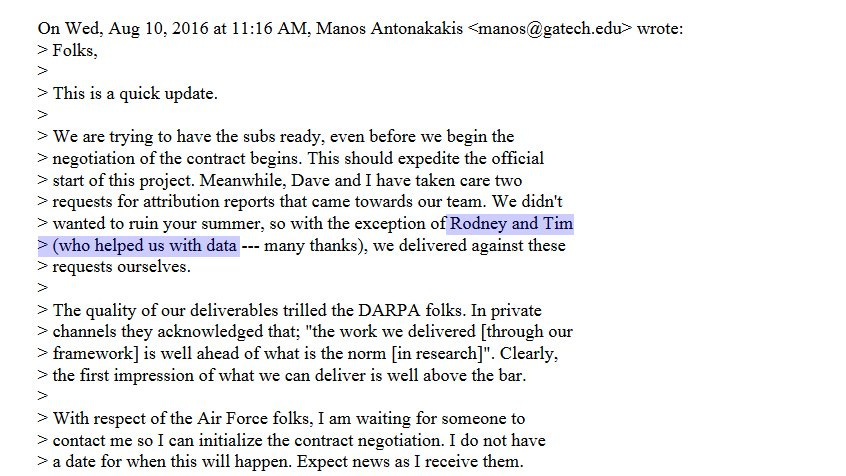
We have extensively covered the apparent role of Dagon and Antonakakis in the DNC hack investigation, and we obtained further confirmation in a letter from DARPA to Senator Grassley with acknowledgement of an August 7, 2016 attribution analysis. We saw one email in our files preceding that date, requesting data from Neustar from a different employee referencing August 7th as the due date. After the date of the attribution analysis, we also had this email:

I followed up with questions making reference to these emails, asking whether Mr. Joffe had provided them data for their DNC hack attribution and asked whether Joffe had ever assisted or reviewed any of their attribution work. Their response follows:
As to your question regarding Mr. Dagon and Dr. Antonakakis’s emails, and how they may have been interpreted, Mr. Joffe never provided them with any data to assist in an investigation of the “DNC Hack”. As we have told you repeatedly and unambiguously, Mr. Joffe had absolutely no involvement or role in the investigation and discovery of the so-called “DNC Hack”. However, as has now become known through public records, as part of a DARPA BAA response, Mr. Joffe, on behalf of Neustar, provided specific data to Mr. Dagon and Dr. Antonakakis at Georgia Tech, so that they could develop algorithms to identify cyber anomalies and attacks IN GENERAL. You have discussed the specific program many times; EA, or Enhanced Attribution. It is quite possible that this data may have been what Mr. Dagon and Dr. Antonakakis were referring to. However, Mr. Joffe had no knowledge, and still has no first-hand knowledge, that this data was used by them or anyone else in any kind of attribution regarding the “DNC Hack”. Further, Mr. Joffe remains unaware of their involvement in any aspect of any “DNC Hack” investigation. They have never discussed it with him.
You generally ask, "Did Mr. Joffe ever assist or review any of the attribution work done by Mr. Dagon or Mr. Antonakakis?” Yes. On occasion, Mr. Joffe was asked to assist or review attribution work that Mr. Dagon and Dr. Antonakakis had undertaken. As you know, Mr. Joffe is considered both a DNS expert (a number of his inventions or developments are in use across the Internet today), and a cybersecurity expert. Over many years, he worked with Mr. Dagon and Dr. Antonakakis on a number of technical, research, and attribution projects. However, for avoidance of doubt or confusion on your part, he has never worked on research or attribution with them or anyone else related to the “DNC Hack”.
For now, we are going to leave this here without offering our analysis. I appreciate the responses from Mr. Joffe, and the significant amount of time spent in responding by his attorney Mr. Tyrrell.



Why would they be honest with you? No reason for them to be. They’re protected by…?
One could say, "treading very lightly." Fairly, I wonder why? Let's keep digging.